Cybersecurity presents a formidable new engineering challenge for the automotive industry. At Horiba MIRA, we see evidence that the convergence of cybersecurity from the enterprise IT sector with the product cybersecurity needs of vehicles and their connected ecosystems causes the automotive sector fundamental problems.
The first of these is how to distinguish cybersecurity for vehicles from corporate IT cybersecurity. The IT industry has contended with cyber threats for approaching half a century and has a mature set of solutions. As a result, it can be erroneously assumed that best practice can be ‘borrowed’ from the solutions developed for wider IT application.
A further problem is that cybersecurity is all too often conflated with safety – indeed, many languages use the same word for both. However, solutions and processes developed for safety engineering are not always appropriate for security or do not scale to contend with automotive cybersecurity threats.
These problems affect all functional levels in the automotive sector. Moreover, cybersecurity is likely to become one of the most pressing near-term issues that the industry must face. Incremental improvements to processes and procedures alone will not overcome the challenges. The entire industry urgently needs to undergo a significant culture shift.
The same – but different
The primary reason why the automotive domain has significantly different cybersecurity challenges to other sectors is that threats to computer systems do not usually precipitate physical harm to victims. The same is not true of automotive cybersecurity, which must contend with this particular threat dimension – and not just harm to vehicle users but also to any third parties using or in proximity to the road transport infrastructure. Moreover, the attack vectors through which such threats are realized are numerous and diverse. For example, as well as familiar attack vectors associated with network connectivity, the manipulation of onboard sensors and external data sources may falsely modify a vehicle’s awareness of its surroundings. This type of attack may not be amenable to traditional intrusion-detection-based approaches, as there is no direct interference with the onboard systems, and in practice a vehicle may not necessarily be able to distinguish between real or spoofed inputs.
A growth business
As cars and light transport have progressively adopted a broad range of functionality, so the average vehicle technology balance is fast becoming far less mechanical and far more digital: onboard processing capability is expanding, as are data volumes and data transmission with V2X and OTA updates increasing, while mechanical subassemblies are simplified as electrification advances.
As vehicles become increasingly autonomous and connected to the infrastructure, the landscape for nefarious cyber interference grows ever wider.
The range of threat agents automotive engineers must consider is also broad, from dishonest users right through to organized crime and rogue states. The motivations of threat agents are also multifarious, from financial fraud potentially perpetrated through onboard payment systems for road charging or parking, to theft of personal data, including geotracking.
Coming, ready or not
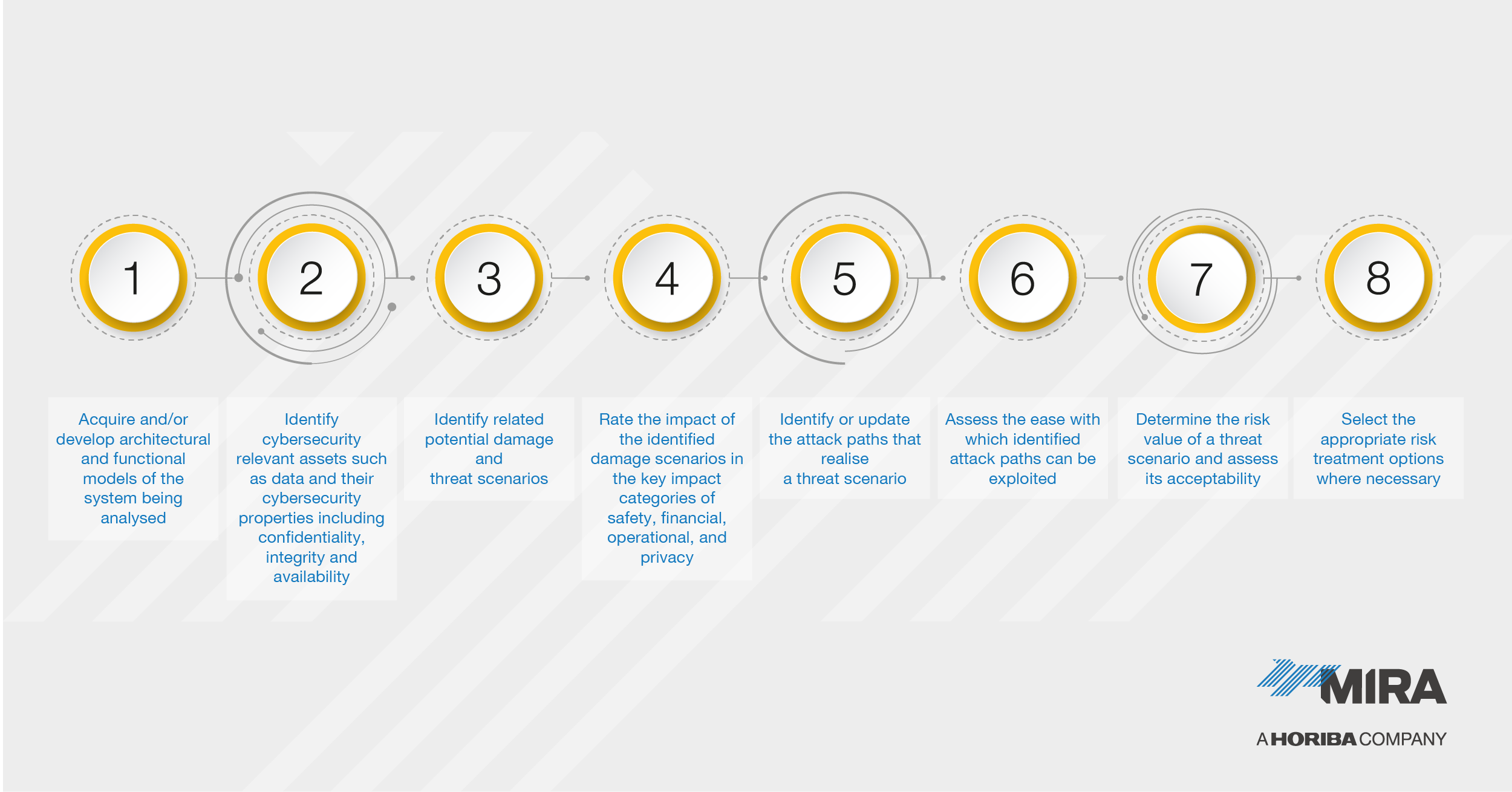
With a rising threat potential and multiple motivations, vehicle and component manufacturers might be tempted to seek solutions from existing systems engineering approaches. However, while cybersecurity might appear to be a logical adjunct to functional safety and the safety of intended functionality (SOTIF), and has several important areas of interaction with those disciplines, it is in fact inherently different. Its scope is far wider than addressing malfunctions that are central to functional safety, or even the insufficient specifications and reasonably foreseeable misuse that are addressed by SOTIF. Rather, it is the intentional abuse by intelligent, adaptive, human adversaries that characterizes cybersecurity attacks and shifts the goalposts beyond just safety considerations to also address privacy, financial and operational concerns. This is why practitioners as much as executives in the industry need to develop solutions expressly focused on cybersecurity engineering rather than placing reliance on best practice from IT or using established systems engineering procedures, which are of course necessary but do not scale to adequately address the challenge in hand.
If this does not provide manufacturers with sufficient motivation to review their approach to cybersecurity, the introduction of new regulations such as UN Regulation 155 and international standards including ISO/SAE 21434 will demand evidence of an upstream ‘security by design’ methodology in engineering practice. Culturally, the shift in emphasis will also have to respond to an entire product lifecycle duty of care to the customer. As the cybersecurity threat landscape is dynamic and new attacks and vulnerabilities will emerge over time, vehicle manufacturers will be obliged to design and manage systems to detect and respond to new threats throughout a vehicle’s operational lifecycle.
For many reasons, automotive cybersecurity bears little relation to its more mature enterprise IT counterpart. Thus it is imperative that the solutions adopted reflect the inherent differences.
Horiba MIRA’s vehicle resilience team has produced two white papers exploring the challenges and solutions for vehicle manufacturers and the tiered supply chain in addressing new cybersecurity requirements. The latest paper, Why Automotive Cybersecurity is Different, is available for free download here.