ATTI talks to Anthony Martin, head of vehicle resilience at Horiba MIRA, to understand new cybersecurity protocols being imposed on the automotive industry.
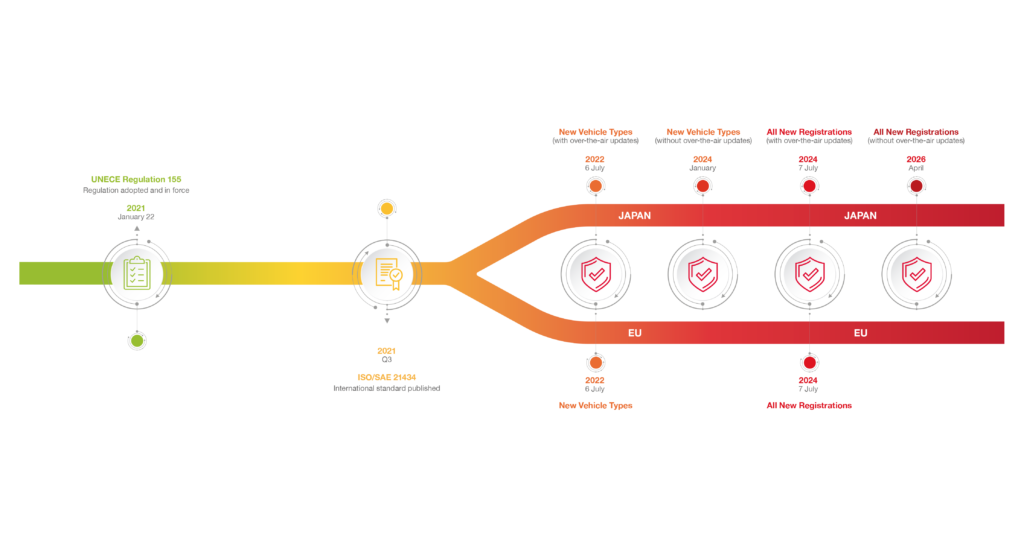
On January 22 this year, quietly and without fanfare, UNECE Regulation 155 was adopted. UNECE is the supranational authority tasked with creating regulatory alignment in many contexts, including the globalized car industry. This alignment is essential to homogenize standards across the diversity of jurisdictions where vehicles are manufactured and the locations where they are ultimately sold and driven.
The need for homogeneous automotive engineering standards has steadily ramped up recently. One reason for this has been the exponential increase in automotive systems that ‘talk’ to other vehicles or the infrastructure. The liabilities presented by these evolving technologies have thrust cybersecurity to the fore. Regulation 155 is intended to provide a uniform set of requirements to guide and govern how manufacturers should contend with the advance of new vehicle functionality that spans everything from ADAS to V2X and even onboard payment systems.
While fighting shy of the corporate panic inflicted by the millennium bug or the imposition of GDPR, cybersecurity engineers at Horiba MIRA believe that Regulation 155 will be a watershed for the automotive industry. Anthony Martin, chief engineer and head of vehicle resilience at Horiba MIRA, has led a team that has been intimately involved in the drafting of the new regulation. He points to five reasons why these changes present a systemic challenge for the industry.
 No type approval, no sale
No type approval, no sale
Of the five red flags Martin believes the industry should heed, the most significant is the adoption of Regulation 155 into national type approvals. The new cybersecurity protocols defined in the regulation will become an embedded element of the validation process carried out by type approval agencies in national markets. And of course, type approval is the process of certification that legitimizes vehicles to be sold. Martin’s warning is stark.
“Regulation 155 will result in new requirements for the type approval process. This has the potential to trip up manufacturers that are unprepared and ultimately means that vehicles that do not meet new approval requirements cannot be sold. For an industry reeling from the impact of the pandemic, no OEM or indeed no tiered supplier can afford another shockwave that affects their capacity to recover,” he says. “Cybersecurity preparation is, therefore, a critical consideration.”
The final countdown
With a clear commercial incentive to embrace the changes required by Regulation 155, another challenge is the immediacy of the new rules taking effect. Adoption through the national type approval process means that markets will work to their own timelines, but as a broad indication of the urgency of the response required, Martin points to the situation in the EU as an example.
“By July 2022 – which is less than 365 working days away – the EU will be mandating cybersecurity compliance through type approvals for all new vehicles in development by OEMs. There is a slightly longer timeframe of an additional 24 months for the requirements to impact existing model lines. Nevertheless, OEMs will have to get their cybersecurity house largely in order by next summer. By virtue of building a full set of services to steer OEMs through the process, we have a well-informed view of how long the process will take. The raw fact is July 2022 is a challenging deadline for any organization that has either not started preparing or lacks a strong leadership commitment to getting the necessary systems in place. The clock is very much ticking,” Martin says.
 Prescription for the pain?
Prescription for the pain?
The third key detail the industry must recognize in relation to the new cybersecurity requirements is that Regulation 155 is not prescriptive. It does not provide a tick-box set of requirements for OEMs to meet; it is instead goal oriented. This means that OEMs must develop their own solutions to meet the intent of the regulation. Too much preparation will incur unwelcome overheads. Too little will mean that the cybersecurity management system (CSMS) implemented will not deliver the required type approval compliance. However, additional pathways to meet the new cybersecurity requirements are in development – in particular the new ISO/SAE 21434 standard – that will provide some assistance for manufacturers to develop an appropriate cybersecurity framework.
A job for life
One particular aspect of the manufacturer’s CSMS is the obligation to provision for continuously emerging cybersecurity threats and provide appropriate remedies. Traditionally, OEM obligations to vehicle purchasers have been finite in duration – for instance, extended warranties have required car makers to maintain a duty of care to customers for periods of perhaps seven years. But the new cybersecurity requirements shift this paradigm into an obligation to manage cybersecurity for the entire vehicle lifecycle – potentially across multiple ownerships – until ultimate decommissioning. This is a substantial new obligation that will require a quantum shift in the way manufacturers maintain relationships with their customers.
Cultivating a culture
The final, critical consideration that Horiba MIRA believes is essential for the industry to navigate the cybersecurity changes that will flow from the new regulation is to look beyond just the procedural enhancements to engineering processes.
As Martin explains, “The changes needed to establish a CSMS and to be able to pass routine cybersecurity audits are pervasive; new approaches will be needed in all phases from vehicle design to test and subsequent operation. But perhaps more importantly, successful solutions to cybersecurity demand a wholesale culture change within organizations. And importantly, this cultural shift has to take place not just in specific functional areas, but everywhere, led by executive commitment. Cybersecurity is here to stay, and solid preparation now will pay dividends in the future.”
To download the white paper click here.



